The practice of stealing data from credit card-embedded chips known as “shimming” evolved from the classic theft of card information that emerged in the early 2010s. Although the scam execution may seem straightforward, the underlying process is challenging.
For instance, scammers or cybercriminals may need a microchip, flash storage, and technology to proceed with the crime. The next stage is to insert the device into the ATM slot, defrauding those using the same ATM to withdraw money. If the cybercriminal succeeds with the plan, the shim inside the slot will copy and store user information of all the cards used in the ATM slot.
This technique is a security risk and presents multiple challenges for defenders. Shimming has gained attention in multiple industries such as banking, manufacturing, and IT, where legacy systems coexist with modern infrastructure.
This article highlights the concept of shimming, how shimming functions, and outlines tips and strategies.
What Is Shimming?
Shimming is a practice that attackers use by inserting a thin layer of code between an application and the operating system. The shim acts as a bridge, intercepting and manipulating system calls or application behaviors for malicious purposes. This shim or malicious software is designed in a way that bypasses security measures providing access to systems.
Most cyber attackers use this method to gain access to sensitive information [passwords, credit card numbers, and other personal information] or eavesdrop on network communication.
In 2023, Statista reported that approximately 13,718 individuals in the U.S. fell victim to credit card and check fraud. Most banking industries are victims of these attacks. Cybercriminals specifically target these industries to get hold of flash memory and microprocessors that store encryption for security purposes.
Gain higher-level access than they would normally be allowed.
Intercept sensitive data as they flow between applications.
Since legacy systems lack modern security measures, cybercriminals tend to exploit the system.
What Are The Different Types of Shimming Attacks?
We have highlighted two types of shimming attacks.
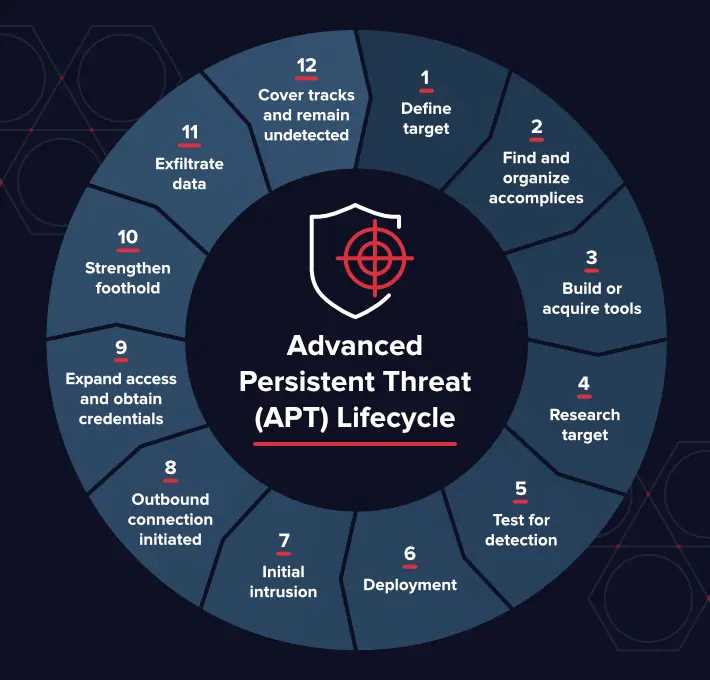
Advanced Persistent Threats (APTs)
APTs have their way into networks to access valuable data based on the user roles. Even before attacking, they might already have their way prepped to compromise the system and take control when no one’s noticing.
Image Source: Varonis
These threats can even access data remotely using multiple commands and control options. How APTs function:
Set up off-net updates and VPN malware to avoid detection.
Plant multiple malware strains to get access to the systems.
Set up multiple C2 destinations to hop in when one shuts down.
Browser-in-the-Middle Shim (BitM)
Cybercriminals cunningly place themselves between the victim’s browser and intended web services to get hold of every communication.
Image Source: CSS Learning Academy
First, the attacker lures the target into trapping them to click a malicious link that redirects them into the attacker’s rigged system. Once the victim takes the bait and clicks on the link, the rigged system takes over the entire operation in the victim’s system.
From this point onward, the attacker eavesdrops on every communication, sensitive data, and other personal information. They use browser proxies to record important communication and information, allowing them to siphon off everything between the victim and the web service.
When the time is right, these attackers intercept all important credentials, sensitive information, email access, and more.
How Shimming Works?
The following steps demonstrate how attackers and cybercriminals use shimming.
Step 1: Introducing “shim”
Attackers use a chip known as “shim” to worm their way into payment systems. These tiny chips act like a microprocessor and a flash drive to stash data. This shim then intercepts legitimate communication between components to either tamper with the data or steal information.
Step 2: Fiddling with the system
The attackers fiddle with systems by inserting the shim card into the ATM card reader, swiping, and copying the victim’s information.
Step 3: Hide the “‘shim”
Attackers then cover the ATM pin pad with plastic, making the system seem normal, and avoiding detection.
Step 4: Steal card details
Attackers use the ATM card slot to wedge another chip to intercept every piece of information from the card.
Step 5: Misuse information
After lifting card data, these attackers use it to reap profits or sell data online.
Attackers have used shimming to bypass multifactor authentication (MFA), alter transaction data in financial applications, and capture login credentials.
What Are The Tips For Protecting Against Shimming Attack?
Given the sophisticated nature of shimming, effective defenses require a layered approach that includes Zero Trust Architecture (ZTA) and microsegmentation.
Zero Trust Architecture (ZTA)
ZTA assumes that threats are already inside the network and implements strict identity verification for every device, user, and application attempting to access resources.
Organizations can establish micro-perimeters around sensitive resources using zero-trust principles. This security measure confirms that only verified and least-privileged traffic is allowed.
Blocking lateral movement minimizes the likelihood of shimming attacks progressing through the network and reaching critical assets.
Microsegmentation
Microsegmentation divides the network into isolated segments. It allows granular control over east-west traffic (internal communication between systems).
Deploying microsegmentation can prevent shims from accessing resources beyond their immediate scope, thus limiting the attack’s blast radius.
NIST SP 800-207 Alignment
NIST’s SP 800-207 framework offers guidelines for implementing a robust Zero Trust architecture. This framework focuses on identity-based access and the continuous verification of all connections and internal communications.
The NIST’s guidelines allow organizations to structure their defenses to detect anomalies caused by shimming activities, such as unexpected traffic flows or unauthorized changes to system behavior.
Conclusion
Shimming is still a growing challenge in cybersecurity. It requires proactive and adaptive defenses. Organizations can effectively mitigate the risks associated with shimming attacks by integrating Zero Trust principles, microsegmentation, and the NIST SP 800-207 framework. This approach not only prevents initial breaches but also limits the spread of malicious activities across different sectors.
Related: How To Become a Database Developer: Step-By-Step Guide
Related: Cybersecurity in the Digital Age: Threats and Safeguards
The post What Is Shimming in Cybersecurity: A Deep Dive appeared first on The Next Hint.